By special guest editor Robyn Robo
It’s an odd feeling writing a review about Hacknet, coming home from my software job while logged into a Linux desktop with a terminal window blinking and notes in my text editor. A browser lies obscured in the background with an email account waiting for attention. I’ve come home from work where there is another setup of the same text editor full of Python and notes, multiple chat and email clients running, log ins to hosting services showing list up list of servers I can access with a click from my terminal manager. Although it’s glitzy Hacknet OS is not quite like any real Unix system I’ve sat down to, it’s also not so far removed as to confuse me.
Everything is identifiable with its real world counterpart and works much the same way. It reminds me of nothing so much as many coworkers’ overly customized OpenBox desktops with carefully colored translucent terminal, borderless square squat windows on triple monitors and an oversized Conky sidebar against a nice dark color scheme that’s easy on the eyes in dimly lit rooms. This game makes me feel a bit like I’m still at work. As a person employed in the computer world, that’s a great achievement. Even the small, constant requests/server-work/reply flow of work is accurate for computer ‘helpdesk’ work.
As you start to play you’ll notice Hacknet’s music is a light techno ambient/trance type of music, extremely suited to the game play. It’s good mood music for productivity, and that’s the type of music you might choose to listen to anyway when trying to be a productive hacker. It’s the kind of music that Spotify would show you as a 70-hour playlist labeled ‘work smart’ or similar.
100 Percent Accurate
I enjoy the dark color scheme, it’s accurate of what I and a probably majority of Linux programmers use every day. On the flipside it’s coated in flashy, unrealistic terminal graphics and glitzed up progress indicators. I can’t judge the game too severly for that as its appearance would otherwise be stuck with a certain drab Spartan sparseness that won’t do for entertainment. The game offers settings that can turn down the graphics and will tone everything down, if the overly graphical GUI glitter gets in your way and distracts you. Hacknet also offers three font sizes which will help if you’re already squinting through an old pair of glasses. There game has the usual kerning/screen tear issues I see on my Ubuntu Linux gaming machine (with the Ubuntu provided NVidia drivers) but overall the game ran dandy. I can happily say there were no crashes though I did see a few people who managed to break things in the Steam forums.
There are no mistakes, just happy little tutorials.
The game starts by throwing you into a pretty solid tutorial, held up by a one-way email conversation with a regret filled software developer. This tutorial starts unfolding a plot that follows you through the game and leaves you by bringing you into ‘contact’ with a group of likeminded hackers. It feels odd to simply ‘reply’ to emails, with nothing in my messages. I’m like a silent JRPG hero but doing so by hitting reply goes against the norms of email so it grinds against my habits like a finger tapping my forehead. There were times I had to add a password or similar detail in my responses so it’s not entirely silence on the player’s part. Regardless, it feels more like crossing off lines in your quest log or silently closing old requests in a company ticketing system than as a meaningful, choice filled interaction with characters on the other side of the wire.
Hacknet takes a very simplistic view of server security. For example, every server’s installation of SSH is always the same, and there are no ancient servers accepting 3DES connections while another requires the latest and greatest implementation of TLS. There’s no real discussion of many practical security measures companies do take, or that people could take at home. No mention that in reality most hackers target outdated systems with junk firewalls first and foremost. I almost feel like it’s a missed opportunity to slyly communicate some personal security knowledge to players. Maybe a white hack add-on campaign of securing, patching and reconfiguring hosts would be educationally worthwhile in the future.

There are no mistakes, just happy little tutorials.
One of the biggest limiting factors in your hacking is RAM. You only have so much with which to actively hack. In many systems you’ll be racing against a clock to remain undetected and launching more processes helps you crack their security faster while eating up RAM. Further, viewing a note or having it open takes up ‘RAM’ on your computer, which is inaccurate as text files of the size they include would be well under a singular megabyte. Those files can be needed though, with essential details available nowhere else in game. Better to play like it’s 1989 and keep a paper notebook. Seeing the memory getting taxed more heavily by a terse ASCII file than by cryptographic processes, which would presumably be loading huge data tables is a bit jarring to anyone with knowledge of how computers work. Further, some little details aren’t quite right, Hacknet always refers to the root directory as “~/” which on a real Unix install would be your user’s home directory and not the top level system directory.
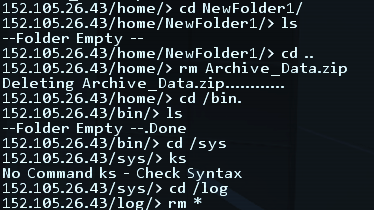
Bad memories of a misplaced ‘rm *’
The Command Line is microscopic in scope compared to its real world Gnu counterparts. Commands are simplified and few in number. For example, you can’t do something like ‘rm /log/df*’ to selectively delete files out of a folder you are not in. Only ‘rm FullFileName’ or ‘rm *’. If you are user of Unix, you will find yourself whacking out commands from muscle memory that fail. It is almost the same feeling as being stuck on a router’s built-in BusyBox terminal. It’s generally not great with wildcards and pattern matching regular expressions. No commands have flags or options, and digging into subdirectories from up top doesn’t quite work right. Again, this is a complaint of too much experience with Unix servers.
The game directs you delete all files in /log/ to eliminate traces of your hacking, this is weird as it would be a dead giveaway that someone had hacked a server in reality. For this very reason, many real world servers run real-time off-system logging. Similarly, the first step most folks do when trying to do anything private online is or should often be to get a good anonymous proxy account, none of that here. Of course, I’ve seen plenty of poorly configured systems that do none of that anyway. Common ports of networked services are accurate which is very pleasant, as I didn’t have to relearn the ‘game’ port of SSH or HTTP. While the full details may be inaccurate, the game really does get the basics of everything right.
I was sad that there doesn’t seem to be any ability to ‘script’ attacks. So for instance you might find yourself repetitively running probe > sshcrack/ftpbounce > porthack to get into a target system, whereas most folks would write a script to do something so repetitive. The same is true when launching a pile of parallel shell processes on systems where access has already been established or deleting logs before disconnecting. Not being able to script adds a repetitive nature to some parts of the game.
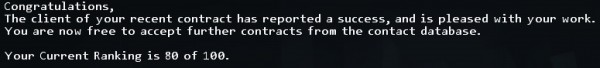
My What?
Another quirk was that working with the first hacking group in the game, Entropy, my rating kept going down in points out of one hundred. No good in game feedback was being provided as to why or whether it is a bad thing or what that rating was. I’m assuming it means I’m missing something important, but there’s no feedback as to why your rating does anything after a mission. It inexplicably does what it does. Worse than that, ratings from a group resetting or wildly jumping about seemed to be a semi-common glitch, according to the games forums. Without feedback as to *why* a rating has changed, noticing if it’s a glitch or not becomes that much harder. I suppose what I’m saying is that this could really use an in game debug process.
The initial hacking group you meet, Entropy, is a collective of ‘gray hat’ hackers. They claim a moral code but seem to take any old job given to them, which is oddly realistic. They’re one of many groups you’ll run into while playing. You can view their message server much the same way as a ticketing system at an IT helpdesk, requests come in, you read the email, fix the problem and reply. I have to say, the way that workflow is so well recreated here is a strange part of the charm.
BRB, HACKING THE GIBSON
The game feels more badass than typing into HackerTyper, and in a great way. The developer got enough right that what I consider inaccuracies are really what they chose to simplify. Everything is much faster than in reality, it makes me think: What are these servers doing, running ‘Shift-Cipher’ encryption for SSH? In reality it’s an essential abstraction for gameplay. Choosing between waiting four weeks for your brute force attack to yield results or paying a shady group for access to their botnet cluster is more realistic, but dull.
I tested all of this on the Linux port that was recently released. That it runs on Linux (and OSX, although I tested on Linux) is a smart move for these folks. All of the keyboard-based commands mean that Steam Console / couch play would be awful so it truly was ported for Linux users. Something of a prime market for this game considering its subject matter.
For someone who isn’t in IT for a living, I could really see this game being fun. It’s reasonably realistic in what it implements. While it doesn’t tell the whole story of modern security & hacking, the bits it does explain tend to be more accurate than not. While I may have pointed out quirks and shortcomings, I was never exasperated by Hacknet in the way media portrayals of hackers leave me. I’ve always found it weird that even in AAA computer games, where at least some of the developers should know better, hacking is portrayed so poorly. This game is a pleasant departure from that while still making you feel like a badass.

